# Unmasking Spam Emails: A Cautionary Overview of Scams
Written on
Chapter 1: Understanding Spam Emails
Spam emails are a common nuisance that most people encounter in their inboxes. Often unsolicited and repetitive, these messages are not just irritating—they can also pose significant threats to your personal information and finances. While some businesses utilize email as a cost-effective marketing tool, it is crucial to handle such communications with caution. In fact, it's often advisable to ignore or refrain from responding to suspicious emails altogether.
Recently, I decided to delve into my spam folder to analyze the nature of these scam emails. What I found was both alarming and amusing, showcasing the tactics scammers use to lure unsuspecting victims. My focus here will be on emails designed to mislead you into divulging sensitive information or financial data, rather than legitimate marketing communications.
Here's a closer look at one of the spam emails I came across.
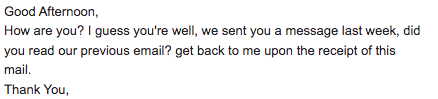
This particular email claimed to follow up on a previous message, trying to entice me to respond for two main reasons: first, to verify if my email account was active, and second, to create a sense of connection. However, there was a red flag—there was no previous message included in the thread. Additionally, the sender used the Bcc field, which is inappropriate for personal communication and indicates a bulk email rather than a targeted message. Always be wary of such tactics.
Section 1.1: Analyzing Further Spam Emails
Another spam message that caught my attention had a more personalized approach.
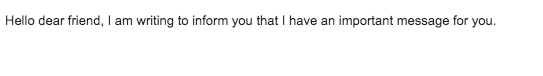
In this case, the sender addressed me as "dear friend," which is a common tactic used to create a false sense of familiarity. However, the message was vague and lacked any substantive information, making it easy to dismiss. Such messages often attempt to lead you into a trap without providing clear details or legitimacy.
Subsection 1.1.1: Recognizing Dangerous Offers
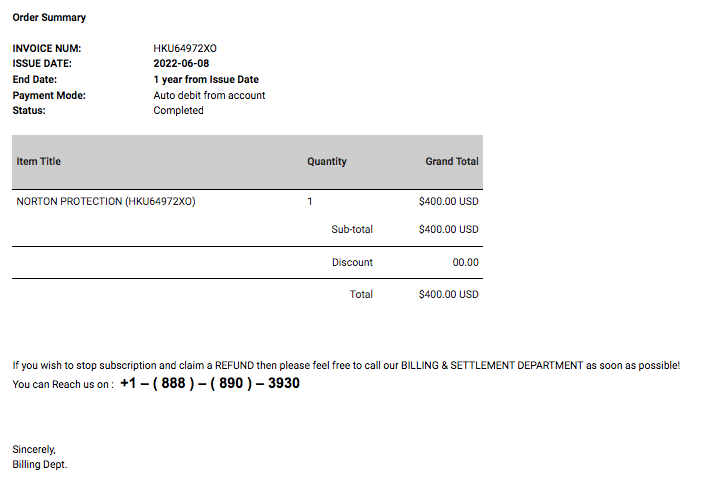
Have you ever encountered a free trial offer that requests your credit card information? I’ve fallen victim to this type of scam before, albeit with legitimate services. These offers often start as free but then charge you without clear notice. Be cautious of emails from free user accounts, as they often carry red flags. The lack of transparency regarding the sender's identity is another warning sign.
Section 1.2: The Scammer’s Targeting Techniques
Scammers often tailor their messages to appeal to specific demographics.
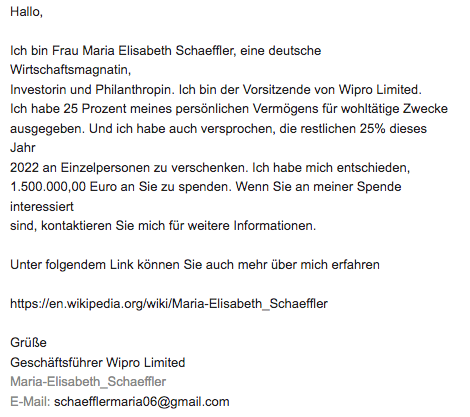
In one such email, the sender targeted a specific audience using language that only a select few would understand. Their attempt to build credibility by including links to Wikipedia was weak, as it lacked personal identification or legitimate company details. While they may include an email signature, without substantial proof of identity, it’s best to remain skeptical.
Chapter 2: The Absurdity of Some Scams
In the video "Level Up Your Emotional Intelligence | Dr. Travis Bradberry," the importance of emotional awareness is discussed, which can be vital when navigating deceptive communications.
One of the most outrageous emails I received claimed to be from Warren Buffet.
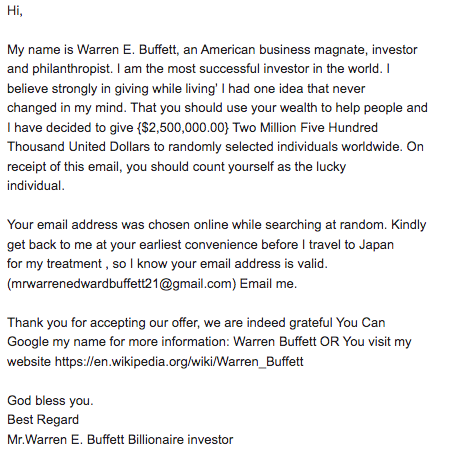
The idea of a global icon reaching out to offer me $2.5 million was absurd. The inconsistencies in the email address and the lack of any clear purpose were immediate red flags. If anyone were to fall for such a scam, it would be hard to fathom.
The video "Terrence Howard is Legitimately Insane" illustrates the importance of critical thinking in assessing unusual claims, a skill that is crucial when evaluating dubious emails.
Even when an email appears nearly legitimate, such as one claiming to be from an estate administrator,
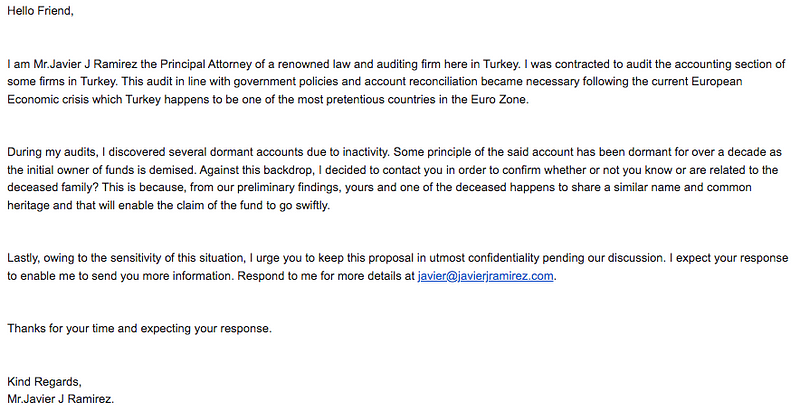
the lack of verifiable evidence about the sender's identity can be a major indicator of fraud. While the email might seem well-crafted, the absence of tangible proof should raise your suspicions.
Key Takeaways
Scammers are everywhere, and it is essential to approach emails with caution. Always scrutinize the messages you receive and perform preliminary checks to protect yourself. If you’re asked for personal information, it’s best to walk away. Stay vigilant and safeguard your information by being aware of the signs of scams.